Secure Account Registration Process
Access Verified Mirror
Begin your secure journey by accessing one of our verified onion links listed above. Each mirror is cryptographically signed with our official PGP key and protected by advanced SSL/TLS encryption. Always verify the PGP signature before proceeding to ensure you're accessing the authentic Black Ops Market platform. Our mirrors are regularly updated and monitored for security threats.
Complete Secure Registration
Fill out our comprehensive registration form with your chosen username and a strong, unique password. All registration data is encrypted using AES-256 encryption before transmission and stored using advanced hashing algorithms. Our system generates a unique salt for each account and implements rate limiting to prevent brute force attacks. Choose a username that doesn't reveal your identity and create a password with at least 16 characters including uppercase, lowercase, numbers, and special characters.
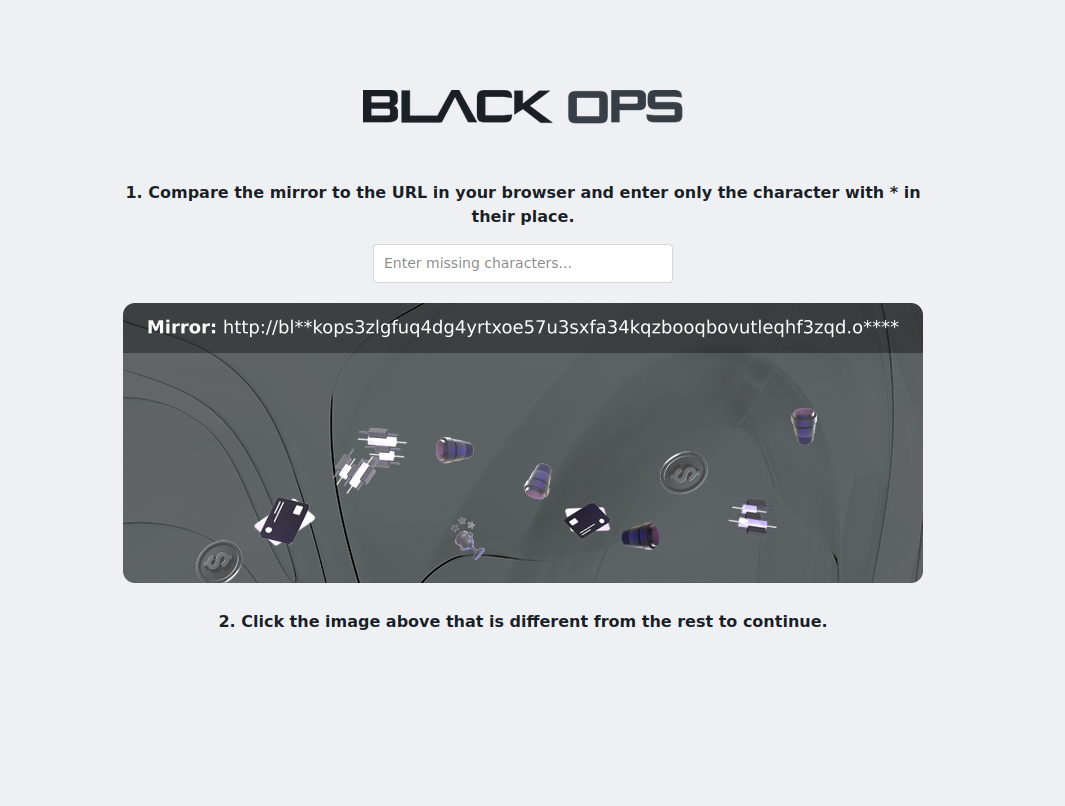
Advanced Security Verification
Complete our sophisticated multi-layer security verification system designed to prevent automated attacks while maintaining user privacy. Our custom CAPTCHA system uses advanced image recognition and behavioral analysis to distinguish human users from bots. This process includes solving visual puzzles, pattern recognition challenges, and timing analysis to ensure legitimate user access while protecting against sophisticated bot networks and automated attacks.
Enable 2FA & PGP Security
Activate two-factor authentication using TOTP (Time-based One-Time Password) and upload your PGP public key for maximum account security. This mandatory step ensures that even if your password is compromised, your account remains secure. Generate a new PGP key pair specifically for marketplace use, and store your private key securely offline. Our system supports RSA keys up to 4096 bits and ECC keys for enhanced security and performance.